The question, “Has Samsung installed ‘unremovable Israeli spyware’ on your phone?” immediately grabs attention, igniting curiosity and concern. This topic delves into the intriguing world of mobile device security, exploring allegations of potentially malicious software pre-installed on Samsung phones. We’ll unpack the initial reactions to these claims, trace their origins, and dissect the technical aspects of “unremovable” software. Prepare for a deep dive into the definition of “spyware,” the investigative procedures, and the potential indicators of compromise.
We’ll examine the security implications, the role of official responses, and the steps users can take to protect their devices. This exploration encompasses a wide range of topics, from forensic analysis techniques to the importance of user behavior in mitigating risks. By the end, you’ll gain a comprehensive understanding of the claims, the technical aspects, and the necessary precautions to safeguard your Samsung phone.
Initial Reactions and Public Awareness

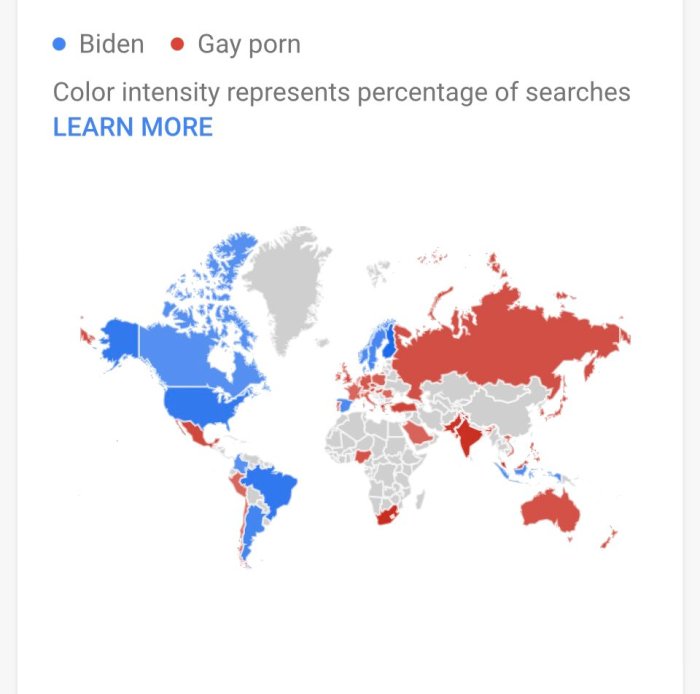
Source: langeek.co
The claim of “unremovable Israeli spyware” on Samsung phones immediately sparked a flurry of activity across the internet. The news, if true, suggested a significant breach of user privacy and national security concerns, leading to a rapid spread of information and misinformation. The public’s initial reactions were a mix of alarm, skepticism, and a strong desire for more information.
Sources of Initial Claims
The initial claims about Israeli spyware on Samsung phones originated from several sources. These sources played a crucial role in disseminating the information and shaping the early public perception of the issue.
- Independent Security Researchers: Often, independent researchers are the first to identify and report vulnerabilities. Their findings, typically shared on personal blogs, security forums, and social media, can trigger widespread discussion. For example, a researcher posting on a platform like X (formerly Twitter) or Mastodon, detailing specific code analysis or observed behavior, could be an early source.
- Tech Blogs and News Websites: Tech-focused blogs and news websites are quick to pick up on these initial reports. They often provide analysis, context, and attempt to verify the claims. Examples include websites specializing in cybersecurity, such as those that publish detailed reports on malware analysis.
- Citizen Journalists and Activists: Individuals or groups concerned with privacy and surveillance often amplify these claims. They may share reports, conduct their own investigations, and advocate for further scrutiny. Their contributions can be particularly influential in raising public awareness.
- Social Media Influencers: Tech-savvy influencers with large followings may also contribute to the spread of information, whether by sharing the findings of researchers or offering their own perspectives on the implications of the claims.
Early Discussions and Debates on Social Media
Social media platforms became the primary battleground for the early discussions and debates. The speed at which information (and disinformation) spreads on these platforms made it a critical space for shaping public opinion.
- X (formerly Twitter): X was a central hub for sharing initial reports, analysis, and user experiences. The platform’s real-time nature and wide reach allowed the claims to quickly gain traction. Hashtags related to Samsung, spyware, and privacy were quickly trending.
- Reddit: Subreddits dedicated to technology, security, and current events became forums for in-depth discussions. Users shared articles, analyzed technical details, and debated the credibility of the claims. For example, subreddits like r/technology, r/privacy, and r/android likely hosted significant discussions.
- Facebook: Facebook groups focused on technology and privacy allowed users to share information and engage in debates, although often with less technical depth than on other platforms.
- Telegram: Telegram channels, particularly those focused on cybersecurity or privacy, became avenues for disseminating information and analysis, often with a focus on anonymity and secure communication.
- Online Forums: Websites like Hacker News and specialized security forums were important in the technical community for discussing the specifics of the alleged spyware.
Key Concerns Raised
The initial stages of public awareness revealed several key concerns that dominated the conversation. These concerns reflected the potential impact on user privacy, data security, and the broader implications for international relations.
- Data Privacy Violations: The primary concern revolved around the potential for unauthorized access to personal data. This included concerns about the collection of location data, contacts, messages, browsing history, and other sensitive information.
- Unremovability of the Spyware: The claim that the spyware was “unremovable” was a major point of alarm. This suggested a sophisticated level of intrusion, making it difficult for users to protect themselves.
- Impact on Security and Trust: If true, the presence of spyware would undermine the security of Samsung devices, potentially exposing users to further attacks and eroding trust in the brand.
- Geopolitical Implications: The involvement of a foreign government (Israel) in the alleged spyware raised questions about the use of technology for surveillance and the potential for international conflicts.
- Lack of Transparency: The lack of official statements from Samsung or the Israeli government fueled speculation and distrust. Users and experts alike demanded transparency regarding the allegations.
- Technical Details and Analysis: The need for detailed technical analysis to verify the claims was a crucial concern. The community wanted to understand how the spyware worked, what data it collected, and how it was installed.
- Potential for Misuse: Concerns were raised about the potential for the spyware to be used for malicious purposes, such as targeting specific individuals, monitoring political opponents, or facilitating espionage.
Understanding “Unremovable” Software
In the context of mobile devices, particularly smartphones like Samsung phones, the term “unremovable” software is often a source of concern. It refers to software that users cannot easily uninstall or remove from their devices using standard methods. This raises questions about user control, privacy, and potential security risks.
Concept of “Unremovable” Software
“Unremovable” software on mobile devices essentially means that the software is deeply integrated into the operating system. Standard uninstall options, like those found in the app settings, are often unavailable. This can be achieved through various technical means, making it difficult for users to remove the software without resorting to more advanced techniques. The primary purpose is often to ensure the functionality of the device or to maintain the relationship between the manufacturer and the user, but it can also be used for other purposes.
Technical Methods for Difficult or Impossible Software Uninstall
Several technical methods can be employed to make software difficult or impossible to uninstall:
- System Integration: Software can be installed as a core part of the operating system (OS). This means it’s treated as a fundamental component required for the device to function correctly. Uninstalling such software could potentially lead to system instability or even render the device unusable.
- Privileged Access: The software might be granted special permissions, allowing it to access and modify system files that are normally off-limits to standard applications. This privileged access can prevent standard uninstall procedures from working.
- Partitioning: Software can be installed on a protected system partition of the device’s storage. This partition is designed to be read-only or highly restricted, making it difficult to modify or remove files stored there.
- Digital Signature Verification: The software may be digitally signed by the device manufacturer or the operating system provider. The OS will verify the signature before allowing any changes. If the signature is valid, modifications are permitted; otherwise, they are blocked. This is a security measure to prevent tampering with the software.
- Dependency on Other System Components: The software may depend on other core system components. Removing it could potentially break the functionality of those dependent components.
Examples of Pre-Installed Software on Samsung Phones and Functionality
Samsung phones, like other Android devices, come pre-loaded with various software. These can be broadly categorized as:
- System Apps: These are essential for the phone’s basic operation. Examples include the dialer, contacts app, settings app, and the camera app. They are crucial for core functionality and generally cannot be removed.
- Samsung Apps: These are apps developed by Samsung. Examples include the Samsung Internet browser, Samsung Health, Samsung Pay, and the Galaxy Store. They offer features specific to Samsung devices and may provide additional services.
- Carrier-Specific Apps: These apps are pre-installed by the mobile carrier. Examples include apps for voicemail, account management, and promotional content. These are often considered bloatware by users.
- Third-Party Apps: These are apps from other companies, pre-installed on the device as part of partnerships or agreements. Examples include social media apps, games, or other utility apps.
The functionality of these pre-installed apps varies widely. System apps provide core functionality. Samsung apps offer device-specific features and services. Carrier apps provide carrier-related services. Third-party apps offer additional functionality, ranging from entertainment to productivity.
Differences in Removal Options for Pre-Installed Software
The removal options available for pre-installed software depend on its type and how deeply it’s integrated into the system. The differences can be summarized as follows:
- System Apps: These apps are typically unremovable using standard methods. The user usually has no option to uninstall them. Disabling is often the only option, which may freeze the app and prevent it from running. Root access may allow for removal, but this voids the warranty and can potentially destabilize the system.
- Bloatware: This category includes carrier-specific and some third-party apps. Uninstalling is sometimes possible, but often only disabling is offered. Root access would enable complete removal.
- Potentially Malicious Software: This category, if it exists, would likely be designed to be very difficult to remove. It may have system-level integration and use the methods described earlier to prevent removal. Root access would be required for removal, and even then, it might be challenging.
Comparison of Removal Methods for Pre-Installed Software
The following table provides a comparison of removal methods for different types of pre-installed software:
| Software Type |
Uninstall |
Disable |
Root Access |
| System Apps |
No |
Yes |
Yes |
| Bloatware |
Sometimes |
Yes |
Yes |
| Potentially Malicious Software |
No |
No |
Yes, but potentially difficult |
Defining “Israeli Spyware”
The term “Israeli spyware,” in the context of mobile devices, evokes concerns about surveillance, data privacy, and potential misuse of technology. To understand these concerns, it’s crucial to define what constitutes “spyware” and how it might be linked to a specific national origin. This section will delve into the technical capabilities of spyware, its potential origins, and the ethical and legal ramifications of its use.
Defining “Spyware” Capabilities
Spyware, in the realm of mobile devices, is software designed to secretly monitor a user’s activity and collect data without their knowledge or consent. Its capabilities can range from relatively benign data collection to highly invasive surveillance. The extent of its capabilities depends on the sophistication of the software and the access it has to the device’s hardware and software.Spyware can perform various actions, including:
- Collecting user data: This includes contacts, call logs, browsing history, and location data.
- Monitoring communications: Spyware can intercept text messages, emails, and instant messages.
- Recording audio and video: It can activate the device’s microphone and camera to record conversations and surroundings.
- Tracking location: Using GPS, Wi-Fi, and cellular data, spyware can track a device’s movements in real-time.
- Accessing files: Spyware can access and copy files stored on the device, including photos, videos, and documents.
- Keylogging: It can record every keystroke made on the device, including passwords and sensitive information.
- Bypassing security measures: Sophisticated spyware can bypass security features like encryption and two-factor authentication.
Identifying “Israeli” Software
Identifying software as “Israeli” is complex, as it involves factors beyond just the country of origin. Several characteristics could suggest an Israeli connection:
- Development Location: The primary development team and company headquarters being located in Israel.
- Funding and Ownership: Significant funding or ownership by Israeli individuals, companies, or government entities.
- Targeted Markets: The software is specifically designed or marketed for use by Israeli government agencies or for surveillance purposes.
- Code Analysis: Analysis of the software code might reveal links to Israeli developers or technologies. However, this is often challenging due to code obfuscation and proprietary software.
- Known Associations: The software has been linked to known Israeli cybersecurity firms or government programs.
It is important to note that these characteristics, individually, do not definitively prove Israeli origin. However, a combination of these factors could suggest a connection.
Legal and Ethical Implications
The use of spyware raises significant legal and ethical concerns. Governments and companies using spyware without proper authorization can face severe consequences.The legal implications include:
- Violation of privacy laws: Spyware often violates data protection regulations such as GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the United States.
- Criminal charges: Deploying spyware can lead to criminal charges, especially if it involves intercepting communications or accessing private data without consent.
- Civil lawsuits: Individuals and organizations affected by spyware can sue the perpetrators for damages, including financial losses and emotional distress.
Ethical considerations include:
- Infringement of human rights: Surveillance through spyware can violate fundamental human rights, such as the right to privacy and freedom of expression.
- Abuse of power: Governments and companies may use spyware to monitor and control individuals, suppress dissent, and gain an unfair advantage.
- Erosion of trust: The use of spyware can erode trust in technology and institutions, leading to a climate of fear and suspicion.
Data Collection Methods
Spyware can employ a variety of methods to collect data from a mobile device. These methods can be broadly categorized as:
- Network interception: Monitoring network traffic to capture data transmitted over the internet, including emails, web browsing activity, and application data.
- API access: Using application programming interfaces (APIs) to access data stored within applications, such as social media platforms and messaging apps.
- Exploiting vulnerabilities: Exploiting security vulnerabilities in the operating system or applications to gain unauthorized access to data.
- Social engineering: Tricking users into installing spyware or providing access to their data through phishing emails or malicious websites.
- Physical access: Gaining physical access to the device to install spyware directly or modify its settings.
Hypothetical “Israeli Spyware” Capabilities
Hypothetical “Israeli spyware,” if it were to exist, might possess the following capabilities:
- Real-time location tracking: Continuous monitoring of the device’s GPS location, even when location services are disabled.
- Encrypted communication interception: Ability to decrypt and read encrypted messages from popular messaging apps.
- Remote microphone activation: Covertly activating the device’s microphone to record ambient sounds.
- Stealth camera activation: Remotely activating the device’s camera to take photos and videos without the user’s knowledge.
- Data exfiltration: Secretly transmitting collected data to a remote server, including contacts, call logs, photos, videos, and browsing history.
- Anti-detection measures: Employing techniques to evade detection by security software and forensic analysis tools.
- Rootkit functionality: Hiding its presence within the operating system to maintain persistence and prevent removal.
Investigative Procedures and Forensic Analysis
Investigating potential spyware on a Samsung phone requires a systematic approach, combining user-level checks with the advanced techniques used by forensic analysts. This section Artikels the steps users can take and the methods employed by professionals to detect and analyze potentially malicious software. It also compares the analysis process between Samsung phones and iPhones and lists organizations specializing in mobile security audits.
User-Level Investigation Procedure
Users can take several steps to investigate their Samsung phones for potentially unwanted software. This procedure focuses on accessible checks that don’t require advanced technical knowledge.
- Check for Unusual Battery Drain: Spyware often consumes battery life. Monitor battery usage in the phone’s settings to identify apps using excessive power. Note any significant changes from your phone’s normal battery consumption patterns.
- Review Data Usage: Spyware can transmit data in the background. Examine data usage statistics in your phone’s settings to identify apps consuming an unusually large amount of data, especially when you are not actively using them.
- Inspect Installed Apps: Review the list of installed apps, looking for unfamiliar or suspicious applications. Research any apps you don’t recognize to determine their purpose and legitimacy. Be especially wary of apps with permissions they don’t seem to need.
- Examine App Permissions: Check the permissions granted to each app. Some permissions, like access to your microphone, camera, or location, can be indicators of potential spyware. Revoke permissions from any apps that seem to be overstepping their bounds.
- Monitor Phone Behavior: Observe your phone’s behavior for any unusual activity, such as unexpected pop-ups, random reboots, or changes to settings you didn’t make. These could indicate the presence of malware.
- Check for Rooting or Jailbreaking: Rooting (Android) or jailbreaking (iOS) can increase the risk of malware infection. Verify your phone’s status to see if it has been rooted or jailbroken, which can make it more vulnerable to spyware.
- Perform a Factory Reset (as a last resort): If you suspect spyware and have exhausted other options, a factory reset can remove it. Be aware that this will erase all data on your phone, so back up your important files beforehand.
Forensic Analysis Tools and Methods
Forensic analysts employ specialized tools and techniques to thoroughly examine Samsung phones for signs of spyware. This involves acquiring the device’s data, analyzing the operating system, and searching for indicators of compromise.
- Data Acquisition: The process of extracting data from the phone is critical. Analysts use techniques like physical extraction (creating a bit-for-bit copy of the device’s storage) and logical extraction (extracting specific data types). Tools like Cellebrite UFED, Oxygen Forensic Detective, and Magnet AXIOM are commonly used.
- File System Analysis: Analyzing the file system reveals the structure of the phone’s data, including installed apps, user files, and system logs. Analysts examine file timestamps, file integrity, and suspicious files to identify potential malware.
- Malware Analysis: Forensic analysts analyze potentially malicious apps or files, using static and dynamic analysis techniques. Static analysis involves examining the code without running it, while dynamic analysis involves executing the code in a controlled environment to observe its behavior.
- Network Traffic Analysis: Analysts examine network traffic logs to identify suspicious network connections or data transmissions. This can reveal communication with command-and-control servers or data exfiltration attempts.
- Timeline Analysis: Creating a timeline of events helps analysts reconstruct the phone’s activity and identify when the spyware might have been installed and what actions it took.
- Memory Analysis: Analyzing the phone’s RAM (Random Access Memory) can reveal running processes, active network connections, and other information that can help identify spyware.
Samsung Phone vs. iPhone Analysis
The analysis process for Samsung phones and iPhones differs due to the operating system differences (Android vs. iOS) and the underlying hardware architectures.
Android (Samsung):
- Android’s open-source nature allows for greater customization, but it also presents more security vulnerabilities.
- Rooting a Samsung phone is possible, which can provide analysts with more control and access to data.
- Forensic tools for Android devices often need to account for the variety of hardware configurations and Android versions.
iOS (iPhone):
- iOS’s closed-source nature provides a higher level of security by default, but it can also make forensic analysis more challenging.
- Jailbreaking an iPhone can provide analysts with greater access, but it can also alter the device’s integrity.
- Apple’s hardware and software are tightly integrated, which can make analysis more consistent across different iPhone models.
Organizations Conducting Mobile Device Security Audits
Several organizations and individuals specialize in mobile device security audits, offering services to assess the security posture of mobile devices.
- Mobile Forensics Firms: Companies like Cellebrite, Oxygen Forensics, and Magnet Forensics offer forensic analysis services and tools for mobile devices.
- Cybersecurity Consulting Firms: Many cybersecurity consulting firms, such as Mandiant (now part of Google Cloud), CrowdStrike, and FireEye, provide mobile security assessments and incident response services.
- Independent Security Researchers: Security researchers and penetration testers, like those at the SANS Institute, often conduct mobile security research and provide security audit services.
- Government Agencies: Law enforcement agencies and government organizations may have their own forensic capabilities for mobile device analysis.
Mobile Forensic Tool Features and Data Collected
Different mobile forensic tools offer varying features and collect different types of data. The following table provides a comparison of key features and data collected by different tools.
| Tool |
Key Features |
Data Collected |
Platform Support |
| Cellebrite UFED |
Physical and logical extraction, advanced data recovery, application analysis, cloud data extraction. |
Call logs, SMS messages, contacts, photos, videos, application data, location data, cloud data. |
Android, iOS, Windows Phone, BlackBerry, and more. |
| Oxygen Forensic Detective |
Physical, logical, and cloud extraction; social media analysis; built-in analytical tools. |
Call logs, SMS messages, contacts, photos, videos, application data, location data, social media data, cloud data. |
Android, iOS, Windows Phone, and more. |
| Magnet AXIOM |
Comprehensive digital forensics platform, file system analysis, timeline analysis, artifact identification. |
Call logs, SMS messages, contacts, photos, videos, application data, location data, web browsing history, email data. |
Android, iOS, Windows, macOS, and Linux. |
| Elcomsoft iOS Forensic Toolkit |
Physical acquisition, password recovery, keychain decryption, iCloud data access. |
Call logs, SMS messages, contacts, photos, videos, application data, location data, iCloud data, keychain data. |
iOS devices. |
Potential Indicators and Symptoms
Identifying potential indicators and symptoms is crucial for detecting spyware on a Samsung phone. While no single symptom definitively confirms the presence of malicious software, a combination of these indicators warrants further investigation. This section explores several technical signs that might suggest a phone is compromised.
Battery Drain Issues
Spyware often operates in the background, consuming resources and impacting battery life. Excessive battery drain can be a significant indicator.Battery drain is often caused by the constant operation of malicious processes.
- Rapid Battery Depletion: If the battery drains significantly faster than usual, even with normal usage, it’s a red flag. Track the battery usage in the phone’s settings to identify which apps are consuming the most power.
- Unexplained Background Activity: Spyware frequently runs in the background, consuming power. Check the battery usage statistics to see if any unfamiliar apps are using a significant amount of battery when not actively in use.
- Overheating: If the phone becomes unusually hot, even when idle, it could indicate that the processor is working overtime, potentially due to hidden processes.
Network Traffic Patterns
Spyware often transmits collected data to remote servers. Monitoring network traffic can reveal suspicious patterns.Analyzing network traffic helps identify data exfiltration.
- Unusual Data Usage: An unexplained increase in data usage, especially when the phone is not actively being used, can suggest data transmission. Monitor data usage in the phone’s settings.
- Connections to Unknown Servers: Spyware often connects to servers with unfamiliar IP addresses or domain names. Use network monitoring tools to identify these connections.
- Frequent Data Transfers: Consistent data transfers, even small ones, to unknown locations, can indicate data being sent from the phone.
- Suspicious Domain Names: Pay attention to domain names that appear unusual or are associated with known malicious activities. Look for misspellings of legitimate domain names or domains that seem random.
Unusual App Permissions
Spyware may request excessive or unnecessary permissions to access sensitive data.Examining app permissions is essential for security.
- Excessive Permissions: Be wary of apps requesting permissions that seem unrelated to their function. For example, a calculator app shouldn’t need access to your contacts or location.
- Suspicious App Behavior: If an app behaves differently than expected, check its permissions. A flashlight app requesting access to your microphone or camera is suspicious.
- Permissions Granted Without Consent: Sometimes, malware may grant itself permissions. Regularly review app permissions in the phone’s settings.
Behavioral Anomalies
A compromised phone may exhibit various behavioral changes.Detecting changes in phone behavior can provide clues.
- Unexpected Pop-ups and Ads: The appearance of unwanted pop-ups and advertisements, even when not browsing the internet, can indicate malware.
- Unexplained App Installations: Spyware may install apps without your knowledge or consent. Regularly check the list of installed apps.
- Performance Issues: The phone may become slow, lag, or freeze more frequently.
- Unusual Text Messages or Calls: Receiving strange text messages or making calls without your knowledge can be a sign of compromise.
- Data Leaks: Data breaches are often a sign of a compromised phone. Look out for any notification of data leaks or unusual activity on accounts linked to your phone.
Security Implications and Vulnerabilities
Source: azureedge.net
The potential presence of spyware on a Samsung phone, especially if it’s “unremovable,” raises significant security concerns. These vulnerabilities could expose users to a range of risks, from data theft and surveillance to device compromise. Understanding these security implications is crucial for protecting personal information and maintaining device integrity.
Vulnerabilities Exploited for Spyware Installation
Several vulnerabilities could be exploited to install spyware on a Samsung phone. Attackers often target known weaknesses in the operating system, applications, or even hardware components.
- Operating System Exploits: Older or unpatched versions of Android, or even vulnerabilities within Samsung’s custom One UI, can be exploited. These exploits could allow attackers to gain elevated privileges, bypassing security measures and installing spyware. For example, a zero-day exploit (a vulnerability unknown to the software vendor) could be used to gain root access, giving the attacker complete control.
- Application Vulnerabilities: Applications, both from the Google Play Store and third-party sources, can contain security flaws. These flaws, such as buffer overflows or improper input validation, can be exploited to inject malicious code. Imagine a popular messaging app with a vulnerability that allows an attacker to execute code remotely.
- Malicious Apps (Trojan Horses): Users might unknowingly install apps that appear legitimate but are actually designed to install spyware. These apps often mimic popular applications, tricking users into granting them permissions that allow for data access and device control. A fake “security update” app, for example, could be a Trojan horse.
- Social Engineering: Attackers can use social engineering techniques to trick users into installing spyware or granting access to their devices. This could involve phishing emails, deceptive websites, or even direct contact, persuading users to click malicious links or download compromised files.
- Network-Based Attacks: Public Wi-Fi networks can be exploited to intercept network traffic. Attackers could use techniques like “man-in-the-middle” attacks to intercept sensitive data, including login credentials, or to redirect users to malicious websites that attempt to install spyware.
Role of Software Updates in Preventing Spyware Installations
Software updates play a critical role in patching security flaws and preventing spyware installations. These updates, released by Samsung and Google, address known vulnerabilities and improve the overall security posture of the device.
- Security Patches: Software updates often include security patches that fix vulnerabilities. These patches close the gaps that attackers could exploit to install spyware. For instance, a patch might address a flaw that allows unauthorized access to the device’s camera or microphone.
- Vulnerability Mitigation: Updates can also include mitigations that make it more difficult for attackers to exploit existing vulnerabilities. These mitigations might involve changes to the operating system or application behavior to reduce the effectiveness of attack techniques.
- Improved Security Features: Software updates introduce new security features. These features could include enhanced malware detection, improved permission management, or stronger encryption. These features add layers of protection, making it harder for spyware to operate undetected.
- Regular Updates are Crucial: It is vital to install updates promptly after they are released. Delaying updates leaves the device vulnerable to known exploits. Users should enable automatic updates whenever possible to ensure they are protected against the latest threats.
Importance of User Behavior in Mitigating Spyware Risk
User behavior is a crucial factor in mitigating the risk of spyware. Even with robust security measures in place, users can inadvertently expose their devices to threats through their actions.
- Avoiding Suspicious Links and Websites: Refrain from clicking links in unsolicited emails, messages, or from untrusted sources. These links could lead to malicious websites designed to install spyware. Always verify the sender and the website’s URL before clicking.
- Downloading Apps from Trusted Sources: Only download apps from the Google Play Store or other reputable sources. Carefully review the app’s permissions before installation. Avoid downloading apps from unknown or untrusted websites, as they may contain spyware.
- Being Cautious with Public Wi-Fi: Use public Wi-Fi networks with caution. Avoid performing sensitive activities, such as online banking or accessing personal accounts, on public networks. Consider using a virtual private network (VPN) to encrypt your internet traffic.
- Regularly Reviewing App Permissions: Review the permissions granted to installed apps regularly. Revoke permissions that seem unnecessary or suspicious. This can help limit the damage if a malicious app is installed.
- Practicing Strong Password Hygiene: Use strong, unique passwords for all accounts and enable two-factor authentication whenever possible. This adds an extra layer of security, even if a password is compromised.
- Keeping the Device Physically Secure: Prevent unauthorized physical access to the device. A stolen or compromised device can be easily exploited to install spyware or access sensitive data.
Security Risks of Rooted Versus Non-Rooted Samsung Phones
Rooting a Samsung phone grants the user administrator-level access to the operating system. While this can offer advanced customization options, it also introduces significant security risks.
- Increased Vulnerability: Rooting bypasses many of the built-in security features designed to protect the device. This makes the device more vulnerable to malware and exploits.
- Malware Installation: Rooted devices are more susceptible to the installation of malicious apps. Root access allows malware to install and operate with elevated privileges, potentially leading to complete device compromise.
- Warranty Voiding: Rooting typically voids the device’s warranty, making it more difficult to receive support or repairs from Samsung.
- Difficulty in Receiving Updates: Rooted devices may have difficulty receiving official software updates. Custom ROMs or modified system files can interfere with the update process, leaving the device vulnerable to older security flaws.
- Data Breaches: Rooted devices are more likely to be targeted by attackers. This increases the risk of data breaches and the theft of sensitive information.
Attack Vectors for Spyware Installation
The following table illustrates different attack vectors that could be used to install spyware on a Samsung phone.
| Attack Vector |
Description |
Example |
Mitigation |
| Malicious Apps |
Installing an app that appears legitimate but contains spyware. |
A fake “battery optimizer” app that steals user data. |
Only install apps from trusted sources; review app permissions. |
| Phishing and Social Engineering |
Tricking a user into clicking a malicious link or downloading a compromised file. |
A phishing email that directs the user to a fake login page. |
Be cautious of unsolicited emails and messages; verify sender and links. |
| Exploiting Operating System Vulnerabilities |
Using a software flaw in the Android operating system to gain access. |
A zero-day exploit that allows remote code execution. |
Keep the operating system updated; use a reputable security solution. |
| Exploiting Application Vulnerabilities |
Using a software flaw in an installed application to install spyware. |
A vulnerability in a messaging app that allows for remote code injection. |
Keep apps updated; avoid installing apps from untrusted sources. |
Official Responses and Statements
The presence of alleged spyware on Samsung devices would undoubtedly trigger a strong reaction from both the company and relevant governmental bodies. Understanding these official responses is crucial for assessing the validity of the claims and the actions taken to address them. This section explores the official communications from Samsung, Israeli government agencies, and the role of security researchers in verifying or debunking the claims.
Samsung’s Official Statements
Samsung’s response to allegations of spyware on their devices would likely be multi-faceted, involving press releases, blog posts, and social media statements. The initial reaction would likely be a denial of the claims, followed by a promise to investigate the matter thoroughly.
- Initial Denial and Investigation: Samsung would likely issue a statement denying the presence of any unauthorized software or spyware on its devices. This initial denial would be followed by an announcement of an internal investigation to determine the veracity of the claims. This is a standard procedure in such situations to maintain consumer trust and protect the company’s reputation.
- Timeline of Responses: The timeline of these responses is critical. The first statement would be a swift response to the initial allegations, followed by updates as the investigation progresses. Subsequent communications might include technical analyses, collaborations with security researchers, and potential software updates to address any identified vulnerabilities.
- Content of Statements: The statements would likely emphasize Samsung’s commitment to user privacy and security, highlighting its existing security measures and its dedication to protecting user data. These statements would also include details about the investigation process, the personnel involved, and the expected timeframe for providing findings.
- Example of a Press Release: A press release might state, “Samsung takes user privacy and security extremely seriously. We are aware of recent allegations regarding the presence of unauthorized software on our devices. We are conducting a thorough investigation, involving our internal security teams and external experts, to determine the accuracy of these claims. We are committed to transparency and will provide updates as soon as they become available.”
Responses from Israeli Government Agencies
If the allegations implicated Israeli government agencies, the response would involve official statements, potential investigations, and collaborations with Samsung.
- Official Statements: Israeli government agencies, if implicated, would likely issue their own statements. These statements would clarify their involvement (or lack thereof) and address the nature of any alleged collaboration with Samsung or other entities. The level of detail provided would depend on the sensitivity of the information and the potential impact on national security.
- Investigative Actions: The Israeli government might initiate its own investigations, potentially involving intelligence agencies or cybersecurity units. The findings of these investigations would be critical in determining the validity of the allegations and any actions required to address them.
- Cooperation with Samsung: If warranted, Israeli government agencies might collaborate with Samsung to assist in the investigation, share information, and ensure the security of Samsung devices used by Israeli citizens or organizations.
- Examples of Statements: A hypothetical statement might read, “The Israeli government is aware of the allegations and is cooperating fully with Samsung in their investigation. We are committed to protecting the privacy and security of our citizens and will take all necessary steps to ensure the integrity of any systems or technologies used by our government.”
The Role of Security Researchers
Security researchers play a critical role in verifying or debunking claims of spyware. Their independent analysis provides unbiased assessments and helps to validate or refute the allegations.
- Independent Analysis: Security researchers would conduct independent analyses of Samsung devices, examining the software, firmware, and network traffic to identify any malicious or unauthorized activity. This analysis involves reverse engineering, malware analysis, and vulnerability assessments.
- Verification of Claims: If the claims of spyware are true, security researchers would provide evidence, such as code samples, network logs, and system artifacts, to support their findings. They would also provide detailed reports on the functionality and potential impact of the spyware.
- Debunking of Claims: If the claims are false, security researchers would provide evidence to debunk the allegations, explaining why the alleged spyware is not present or why the evidence is misinterpreted.
- Public Reporting: Security researchers would typically publish their findings in public reports, blog posts, or academic papers. These reports would provide detailed technical information and allow other researchers to verify the findings. They often present their research at security conferences, sharing their knowledge with the wider community.
- Examples of Research: A security researcher might publish a report detailing the analysis of a suspicious application found on a Samsung device. The report could include a description of the application’s behavior, its network communication, and its potential impact on user privacy. Another researcher might present their findings at a conference, explaining the vulnerabilities found in the device’s firmware and how they could be exploited to install spyware.
Hypothetical Official Samsung Statement
“Samsung is committed to the security and privacy of our users. We are aware of the recent allegations regarding potential spyware on our devices. We have initiated a thorough investigation, involving our internal security teams and leading external cybersecurity experts. Our priority is to determine the accuracy of these claims and to take immediate action if any vulnerabilities are identified. We will provide regular updates on our findings and any steps we are taking to protect our customers. We are dedicated to maintaining the trust of our users and ensuring their data is secure.”
User Actions and Mitigation Strategies
Protecting your Samsung phone from potential spyware requires a proactive approach. While the allegations of unremovable spyware are serious, there are steps users can take to enhance their device’s security and minimize risks. This section provides practical guidance on safeguarding your device and responding to potential threats.
Steps for Protecting Your Phone from Potential Spyware
Taking immediate action is crucial for your phone’s security. It’s essential to understand and implement a layered approach to security.
- Keep Your Software Updated: Regularly update your Samsung phone’s operating system (One UI) and all installed apps. Updates often include security patches that address known vulnerabilities. Go to Settings > Software update > Download and install.
- Be Cautious of App Downloads: Only download apps from the official Google Play Store. Avoid sideloading apps (installing from unofficial sources), as these can contain malware. Always review app permissions before installation.
- Review App Permissions Regularly: Periodically check the permissions granted to each app. Revoke any unnecessary permissions, especially those related to location, microphone, camera, and contacts. Go to Settings > Apps > [Select App] > Permissions.
- Use Strong Passwords and Biometrics: Employ a strong password or PIN for your phone and enable biometric authentication (fingerprint or facial recognition) for added security. Avoid using easily guessable passwords.
- Enable Two-Factor Authentication (2FA): Activate 2FA on all your important accounts, including your Google account and any cloud services you use. This adds an extra layer of security, even if your password is compromised.
- Use a VPN: Consider using a Virtual Private Network (VPN) when using public Wi-Fi networks. A VPN encrypts your internet traffic, protecting your data from eavesdropping.
- Be Wary of Phishing Attempts: Be vigilant against phishing attempts via email, SMS, or phone calls. Do not click on suspicious links or provide personal information to unknown sources.
- Monitor Your Data Usage: Regularly check your phone’s data usage to identify any unusual activity. Excessive data consumption could indicate the presence of spyware. Go to Settings > Connections > Data usage.
- Back Up Your Data Regularly: Regularly back up your phone’s data to a secure location (e.g., your Google account or an encrypted external drive). This allows you to restore your data if your phone is compromised or needs to be reset.
- Educate Yourself: Stay informed about the latest security threats and best practices. Read security blogs, follow reputable cybersecurity experts, and understand the risks associated with different types of malware.
Factory Resetting a Samsung Phone and Impact on Pre-installed Software
A factory reset is a powerful tool for removing malicious software. It’s important to understand the process and its implications.
A factory reset returns your phone to its original state, as it was when you first purchased it. This process wipes all user data, settings, and downloaded apps. However, it does not always remove pre-installed software, especially if it’s deeply integrated into the system.
Here’s how to factory reset a Samsung phone:
- Back up your data: Before you begin, back up all your important data, including photos, videos, contacts, and documents, as a factory reset will erase everything.
- Go to Settings: Open the Settings app on your Samsung phone.
- Navigate to General management: Scroll down and tap on “General management.”
- Select Reset: Tap on “Reset.”
- Choose Factory data reset: Tap on “Factory data reset.”
- Review the information: Read the information on the screen, which will warn you that all data will be erased.
- Tap Reset: Tap the “Reset” button to begin the process.
- Enter your PIN or password: You may be prompted to enter your PIN or password to confirm.
- Tap Delete all: Tap “Delete all” to confirm and start the factory reset. The phone will restart and erase all data.
Impact on Pre-installed Software:
Factory resetting your Samsung phone will typically remove most user-installed apps and data. However, it may not remove all pre-installed apps. Some pre-installed apps, particularly those integrated into the system (such as core Samsung apps or those from your mobile carrier), may remain after the reset. This is because they are considered part of the operating system image.
Important Note: While a factory reset can help remove some spyware, it is not a guaranteed solution. Sophisticated spyware might persist if it has been deeply embedded in the system. After a factory reset, it is essential to monitor your phone for any unusual behavior.
Verifying the Integrity of Samsung Phone Software Through Official Channels
Verifying your phone’s software integrity is essential to ensure that it hasn’t been tampered with. Samsung provides several official channels for verification.
Using Samsung’s Official Software Update Channels:
The primary way to verify the integrity of your phone’s software is by receiving updates through Samsung’s official channels. These updates are digitally signed by Samsung, ensuring that they come from a trusted source and haven’t been modified. When you update your phone’s software through the “Software update” option in the Settings app, the phone automatically verifies the integrity of the update package before installing it.
Checking for Software Updates Regularly:
Regularly check for software updates. Samsung releases security patches and software updates that address vulnerabilities and improve the security of your device. These updates often include fixes for known security issues. Go to Settings > Software update > Download and install.
Using Samsung’s Support Website and Tools:
Samsung’s official website provides support resources, including software and firmware downloads. You can use these resources to download the correct firmware for your phone model and verify its authenticity. However, this process is usually more technical and intended for advanced users. It involves manually flashing the firmware onto your phone using a computer and specialized software. Before doing so, be sure to back up all of your data.
Contacting Samsung Support Directly:
If you have any concerns about your phone’s software integrity, contact Samsung’s official customer support channels. They can provide guidance and assistance in verifying your device’s software. Samsung support can also guide you on how to check your phone for any unauthorized software.
Reporting Suspected Spyware to Relevant Authorities or Organizations
Reporting suspected spyware is crucial for combating digital threats. Various authorities and organizations can investigate and take action.
Reporting to Law Enforcement:
If you suspect that your phone has been infected with spyware, especially if you believe your data has been compromised or if you suspect criminal activity, report it to your local law enforcement agency. They can investigate the incident and potentially identify the perpetrators. Provide as much detail as possible, including the date, time, and any specific behaviors that make you suspicious.
Reporting to Cybersecurity Organizations:
Organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) in the United States or the National Cyber Security Centre (NCSC) in the United Kingdom provide resources and support for reporting cyber incidents. They can provide advice and assistance. These organizations often collect information about cyber threats to help track and prevent attacks.
Reporting to Samsung:
Contact Samsung’s customer support or security team to report your concerns. Provide details about the suspected spyware, any unusual behavior you’ve observed, and any evidence you’ve collected. Samsung may investigate the issue and take appropriate action. They can provide advice and, if necessary, assist you in taking steps to secure your device.
Reporting to Consumer Protection Agencies:
In cases of consumer fraud or deceptive practices, report the issue to your local consumer protection agency. They can investigate potential violations of consumer laws. Provide any documentation or evidence you have, such as purchase receipts or communications with the vendor.
Comparison of Security Software Solutions for Samsung Phones
Choosing the right security software can significantly improve your phone’s protection. The following table compares some available solutions.
| Security Software |
Key Features |
Pros |
Cons |
| Samsung Knox |
Real-time protection, secure folder, hardware-level security, data encryption. |
Deep integration with Samsung hardware, strong security features, included with most Samsung devices. |
Limited features for non-Samsung devices, may not offer as many advanced features as dedicated security apps. |
| Google Play Protect |
Malware scanning, app security checks, safe browsing. |
Free, built-in to Android, scans apps from the Google Play Store. |
Limited features compared to dedicated security apps, may not catch all threats. |
| Third-Party Antivirus Apps (e.g., McAfee, Norton, Bitdefender) |
Malware scanning, real-time protection, anti-theft features, VPN, privacy tools. |
More comprehensive protection, advanced features, regular updates. |
Can impact battery life and performance, may require a subscription. |
End of Discussion

Source: askdifference.com
In conclusion, the investigation into the presence of “unremovable Israeli spyware” on Samsung phones is a complex one, involving technical analysis, user awareness, and official responses. From initial claims to forensic examinations, the topic highlights the importance of understanding mobile device security. The journey through potential indicators, security vulnerabilities, and mitigation strategies reveals the proactive steps users can take. Ultimately, this exploration serves as a reminder of the need for vigilance and informed decision-making in the digital age, emphasizing the critical role of users in protecting their data and privacy.
Essential Questionnaire
What is “unremovable” software?
It refers to software on a device that cannot be uninstalled through standard methods, like the app settings menu. It’s often deeply integrated into the operating system.
What does “spyware” do?
Spyware is software designed to secretly collect information about a user’s activities and send it to another party. This can include tracking location, monitoring calls, accessing messages, and more.
How can I check if my Samsung phone has spyware?
You can look for unusual battery drain, excessive data usage, unfamiliar apps, and strange network activity. Forensic tools and security experts can provide a more thorough analysis.
What should I do if I suspect spyware?
Back up your important data, reset your phone to factory settings, and monitor its behavior afterward. Consider contacting a security expert for further investigation.
Are all pre-installed apps spyware?
No, many pre-installed apps are essential for the phone’s functionality. However, some could potentially be exploited or contain vulnerabilities. The key is to differentiate between necessary system apps and potentially malicious ones.